CVE-2024-6098 / ICSA-24-228-11 KEPServer, TOP Server ControlLogix Automatic Tag Generation Vulnerability
CVE-2024-6098 / ICSA -24-228-11 affects a 6.x versions of TOP Server and KEPServerEX
Technical Details:
When performing an online tag generation to devices which communicate using the ControlLogix protocol, a machine-in-the-middle, or a device that is not configured correctly, could deliver a response leading to unrestricted or unregulated resource allocation. By default, these functions are turned off, yet they remain accessible for users who recognize and require their advantages.
Mitigation:
Software Toolbox recommends users take a defense-in-depth stance with regards to their manufacturing networks ensuring proper access control is maintained. Additionally, adherence to the TOP Server Secure Deployment Guide will minimize this threat through accurate configuration and use of the product. We also recommend that users follow CISA recommended practices for securing Industrial Control Systems (ICS).
It is recommended that customers leveraging Automatic Tag Generation enable the Impose Array Limit field in Logix Database Settings and set an Array Count Upper Limit that aligns with the projects anticipated size.
• Right click on Device > Properties > Logix Database Settings
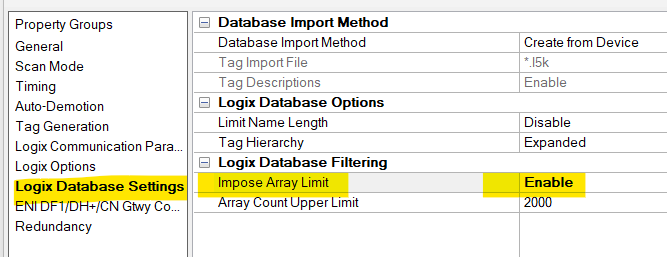
• Right click on Device > Properties > Logix Database Settings

If you have a question regarding this advisory, please submit a support inquiry.
![SWTB_logo_rgb_color_mode-wPadding-2000x961.png]](https://help.softwaretoolbox.com/hs-fs/hubfs/SWTB_General/Images/Press_Kit/SWTB_logo_rgb_color_mode-wPadding-2000x961.png?height=50&name=SWTB_logo_rgb_color_mode-wPadding-2000x961.png)